Server environments run business-critical applications, hold sensitive data, and provide access to distributed networks. They sit at the core of every enterprise IT ecosystem, making them a target for attackers. Server hardening applies to any IT system, including servers, networks, and applications. Relying on default settings can expose an IT system to vulnerabilities and increase the risk of exploitation.
Misconfigurations, weak access controls, or outdated policies can quickly become entry points for breaches, including data breaches. Traditional patching addresses vulnerabilities, but configuration drift and overlooked settings often leave gaps. Following key steps in server hardening is essential for protecting business-critical IT systems. Server hardening reduces the attack surface and enforces consistent security controls, enabling organizations to establish a stronger, more reliable defense. With the scale and complexity of today’s hybrid environments, automation is key to making hardening practical, and that’s precisely what BigFix Compliance delivers.
What is Server Hardening?
Server hardening is the process of reducing a server's vulnerabilities by configuring it to minimize its attack surface. This typically includes enforcing strong authentication (such as requiring unique passwords), disabling unused services, ensuring correct file permissions, applying industry-standard security policies, and managing security configuration and system configuration settings. In practice, hardening transforms a default system into one that actively resists intrusion and remains resilient against both malicious and accidental changes.
Why is Server Hardening Important?
Hardening ensures servers remain trustworthy foundations for enterprise workloads. Beyond improving security posture, hardened servers:
- Help organizations meet industry regulations such as HIPAA, PCI-DSS, or NIST by following compliance standards and frameworks that provide the structure for achieving regulatory goals.
- Protect critical data and workloads against downtime or breaches, supporting operational continuity by minimizing service interruptions.
- Provide confidence to management, auditors, and regulators that systems are consistently secure.
For organizations with distributed, hybrid IT environments, proper server hardening and endpoint compliance are the foundation of enterprise security posture.
The Challenge of Server Hardening
When we think of keeping any system secure, the first thing that comes to mind is patching. However, Server Hardening is the process of enhancing server security through various means, resulting in a significantly more secure server operating environment.
For servers, there are numerous elements—possibly hundreds—that need to be monitored to ensure that potentially sensitive data or access to such data is not exposed or compromised. Typical elements include:
- Are password requirements stringent enough to withstand brute-force hacks?
- Are file permissions or ownership settings on non-Windows servers configured adequately for key system files, or have they been compromised?
- Is antivirus software running?
There can be tens or hundreds of items like these that may need to be monitored on EACH SERVER. Since an average systems administrator is likely responsible for up to 100 (or more) servers, it quickly becomes apparent how unmanageable and unrealistic it is to expect them to audit/monitor each server manually. BigFix Compliance can automate these checks for system administrators, thus making your servers more secure.
The Server Hardening Process:
The hardening journey follows a cycle:
- Assess the server’s current configuration.
- Compare against security baselines such as CIS or PCI.
- Remediate deviations to restore systems to compliance.
- Monitor continuously to detect drift and achieve continuous compliance through ongoing monitoring and remediation.
- Report to stakeholders for validation and audit readiness.
These reporting forms are a crucial component of effective compliance management, enabling organizations to maintain visibility into their security posture while meeting regulatory and audit requirements.
At scale, organizations require server hardening software to automate these steps and ensure consistency across diverse environments. BigFix automates this process across operating systems, enabling scale that manual approaches can’t match.
Reducing the Attack Surface
Reducing the attack surface is a foundational element of server hardening, directly impacting your organization’s security posture. In essence, system hardening means identifying and eliminating unnecessary services, ports, and protocols that attackers could exploit. By minimizing the number of potential entry points, you limit access to sensitive data and system components, making it significantly harder for unauthorized users to compromise your servers.
A comprehensive server hardening process begins with a thorough review of system configurations, user accounts, and physical access controls. Only authorized personnel should have access to critical systems, and this is best achieved by securing physical access—housing servers in controlled environments such as data centers or locked server rooms. Implementing role-based access control and multi-factor authentication further ensures that only those with a legitimate need can interact with sensitive areas of your IT environment.
Enforcing secure configurations is another critical step in reducing the attack surface. This includes setting up firewall rules to permit only necessary network traffic, disabling unnecessary services and software, and requiring strong passwords and unique authentication mechanisms for all user accounts. Regularly reviewing and updating security policies and procedures ensures your security measures remain aligned with industry standards and best practices.
Operating system hardening (OS hardening) is vital in this context. Keeping your operating systems up to date with the latest security patches, disabling default or unnecessary features, and applying secure configurations all help reduce the risk of security vulnerabilities. Leveraging configuration management tools and security hardening tools can automate the enforcement of these secure configurations, detect and remediate configuration drift, and provide continuous monitoring for emerging threats.
Adhering to compliance frameworks such as PCI DSS and CIS benchmarks provides a structured approach to system hardening. These industry standards offer detailed guidelines for securing server configurations and protecting sensitive data, helping organizations maintain a strong security posture and meet regulatory requirements.
Understanding Your Overall Compliance Posture
One of BigFix Compliance's functions, in addition to auditing and enforcing hardening elements, is to provide a view of your overall compliance. It provides a dedicated reporting engine that periodically collates all audit results from your endpoints into graphs and reports, showing trends. Using the dashboard and reports, management, application teams, and auditors can quickly understand the state of endpoint security and compliance across the enterprise.
The Compliance Analytics and Reporting engine provides a variety of report views. The Compliance Overview report, shown in Figure 1, allows authorized report consumers to quickly drill down into any aspect of compliance that interests them. Role-Based Access Controls (RBAC) ensure that users can only view compliance data that aligns with their job role.
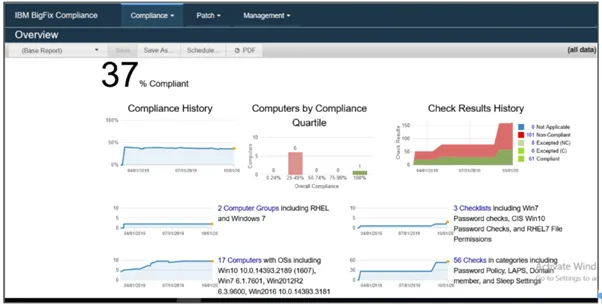
Figure 1: Example of Compliance Overview report
How are Compliance Statistics Calculated?
Compliance statistics, such as the compliance percentage, are calculated from the results of ongoing compliance audits conducted on endpoints using custom checklists. A custom checklist is a specific set of individual checks drawn from the extensive library of checks. Figure 2 is a sample of available checklists in BigFix Compliance. The library includes checks for various operating systems and applications, originating from organizations such as the Center for Internet Security (CIS), the Defense Information Systems Agency (DISA), and the Payment Card Industry (PCI). Although each check includes a default, recommended audit value, most can be changed to fit individual needs.
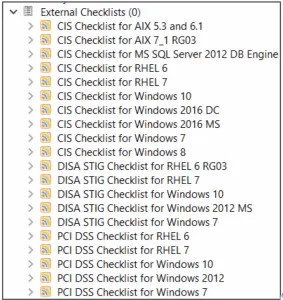
Figure 2: Sample of available compliance checks
Within a checklist, there are individual, specific checks available. Figure 3 depicts a sampling of CIS checks for Windows 10 (on the left) and checks for Red Hat Enterprise Linux 7 (on the right).
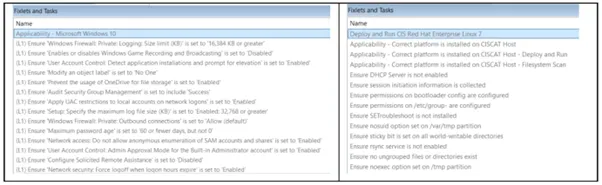
Figure 3: Sample CIS Windows 10 and RHEL 7 checks
Server Hardening Checklist:
BigFix includes an extensive library of compliance checklists drawn from authoritative bodies, such as CIS, DISA, and PCI. A typical checklist may cover:
- Account Security: Password history, minimum length, lockout thresholds.
- System Integrity: Ownership and permissions on sensitive files.
- Protection Services: Antivirus and firewall enabled and up to date.
- Configuration Settings: Registry values, kernel parameters, and audit policies.
- Monitoring Controls: Centralized logging, log retention, and access reviews.
These checklists can be customized to reflect organizational needs, then deployed at scale. Each system continuously evaluates itself against the checklist and reports deviations.
BigFix provides a set of wizards that enable the easy creation and maintenance of custom checklists. In Figure 4, a wizard is used to create a custom checklist called "Windows 10 Password Checks."
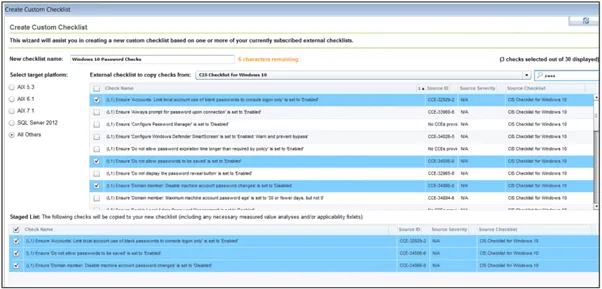
Figure 4: Example of building a custom checklist using a wizard
After a checklist is built, the default, recommended values for each check can be changed as desired before the checklist is applied to a specific set of endpoints. Once the custom checklist is applied to a set of endpoints, each endpoint agent continually assesses itself against the audit checks. Initially, the agent reports back the compliance status for each check. Afterwards, the agent reports only changes in compliance status, thereby minimizing bandwidth usage. The BigFix Compliance Analytics server uses the results of these checks to generate the Compliance reports.
Using BigFix terminology, a check is implemented as a Fixlet™. A Fixlet comprises a set of targeting rules that identify which endpoints it applies to or is relevant to, and a set of BigFix Actions that define the action to be taken by the agent.
Each Targeting Rule is a Boolean test that defines a condition for a fixlet applicable to or relevant to an endpoint. All specified Targeting Rules or conditions must be ‘true’ before the fixlet is considered relevant. Similarly, BigFix Actions can take virtually any action on an endpoint. For example, a BigFix action could initiate a reboot of the endpoint or change a registry value on a Windows endpoint.
How is Non-compliance Remediated?
The BigFix agent reports out-of-compliance conditions (checks) as described above. By default, the BigFix agent only reports non-compliance conditions. However, in most cases, it is also desirable for the agent to remediate an out-of-compliance condition, either one time or continuously, returning the endpoint to the desired state. A BigFix Administrator can enable remediation actions for any Fixlet using BigFix’s Take Action wizard. Using remediation actions, systems are always kept in compliance without manual intervention.
Can Multiple Checklists be Combined?
More than one set of checks may apply to any given set of endpoints. Multiple checklists can be bundled together into a Baseline and deployed as a single action, minimizing the effort of system administrators. Each check in the baseline will be evaluated and potentially remediated independent of any other checks in the deployed baseline. By deploying a baseline, a single administrator action can continuously audit and remediate hundreds of audit checks, ensuring compliance across all endpoints.
Best Practices for Ongoing Hardening
While automation simplifies the mechanics of server hardening, organizations benefit from adopting a few practices to keep security strong over time:
- Standardize Hardened Builds: Begin with secure server images to prevent new deployments from introducing variation.
- Automate Remediation: Enable continuous actions compliance without manual intervention. Incorporating a patching tool into this automation ensures that vulnerabilities are addressed quickly while configurations remain aligned with compliance baselines.
- Update Baselines Regularly: Refresh checklists to reflect new security threats and evolving regulatory standards.
- Integrate with IT and SecOps Workflows: Treat hardening as part of everyday operations, not a one-off project.
When combined with BigFix Compliance, these practices ensure that hardened servers remain consistently secure and compliant, not just at the point of deployment.
Summary
Server Hardening is the process of enhancing server security to create a secure server operating environment that is less prone to security attacks and data breaches. Hardening servers and keeping them in compliance can be a daunting task for system administrators, as there are often hundreds of elements to monitor. When servers experience configuration drift, through malicious or unintentional actions, they can fall out of compliance. Checking for compliance and remediating non-compliance can be very time-consuming and a seemingly endless task. With BigFix Compliance, continuously monitoring compliance and automatically remediating issues are easy. Additionally, BigFix Compliance a set of dashboards and reports to assess endpoint compliance, delivering critical information to all stakeholders responsible for enterprise security.
Frequently Asked Questions
1. What is service hardening?
Service hardening is the process of restricting or disabling unnecessary services when you harden a server. It ensures that only essential functions remain active, thereby minimizing the attack surface and reducing opportunities for exploitation. In the lifecycle of server setup, service hardening follows the initial build stage and focuses on configuring the server securely for long-term, compliant operation.
2. What is the purpose of hardening?
The purpose of hardening is to establish a secure baseline for servers and endpoints. By enforcing consistent configurations and reducing vulnerabilities, organizations protect sensitive data, meet regulatory requirements, and ensure ongoing compliance.
3. What is the best endpoint management software?
The most effective solutions combine endpoint management with compliance automation. HCL BigFix enables organizations to manage and secure diverse operating systems from a single console while enforcing compliance policies in real-time.
4. What is server application hardening?
Server application hardening involves securing the applications that run on top of a server, such as databases or web services. This includes applying vendor-recommended security settings, enforcing access controls, and ensuring that applications comply with organizational policies.
Start a Conversation with Us
We’re here to help you find the right solutions and support you in achieving your business goals.







